AI-Powered Threat ModelingThat Scales
Ship faster in the AI-era while handling breaches at design time. We build the practice, integrate the tools, and train your team to run it.
Schedule a Consultation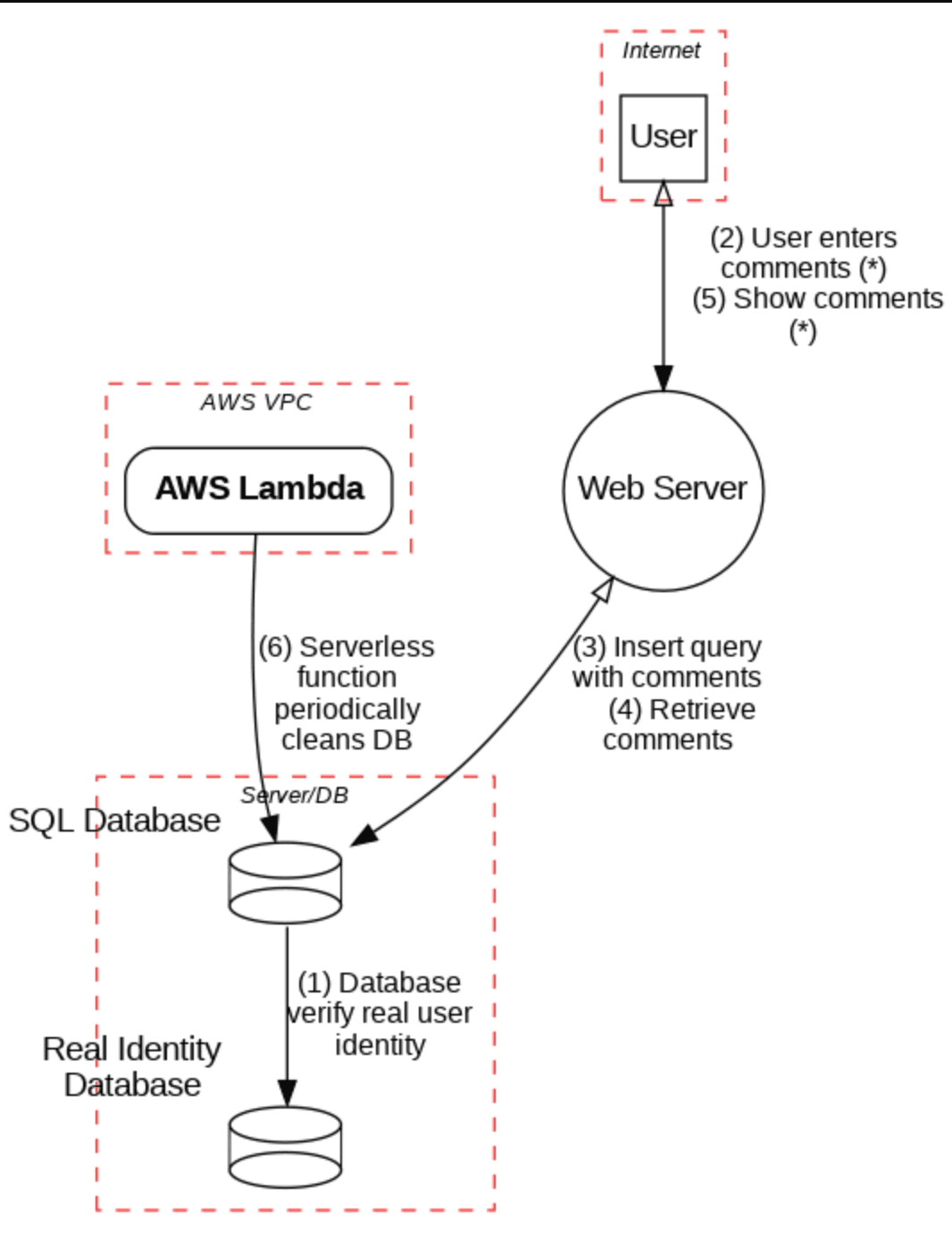
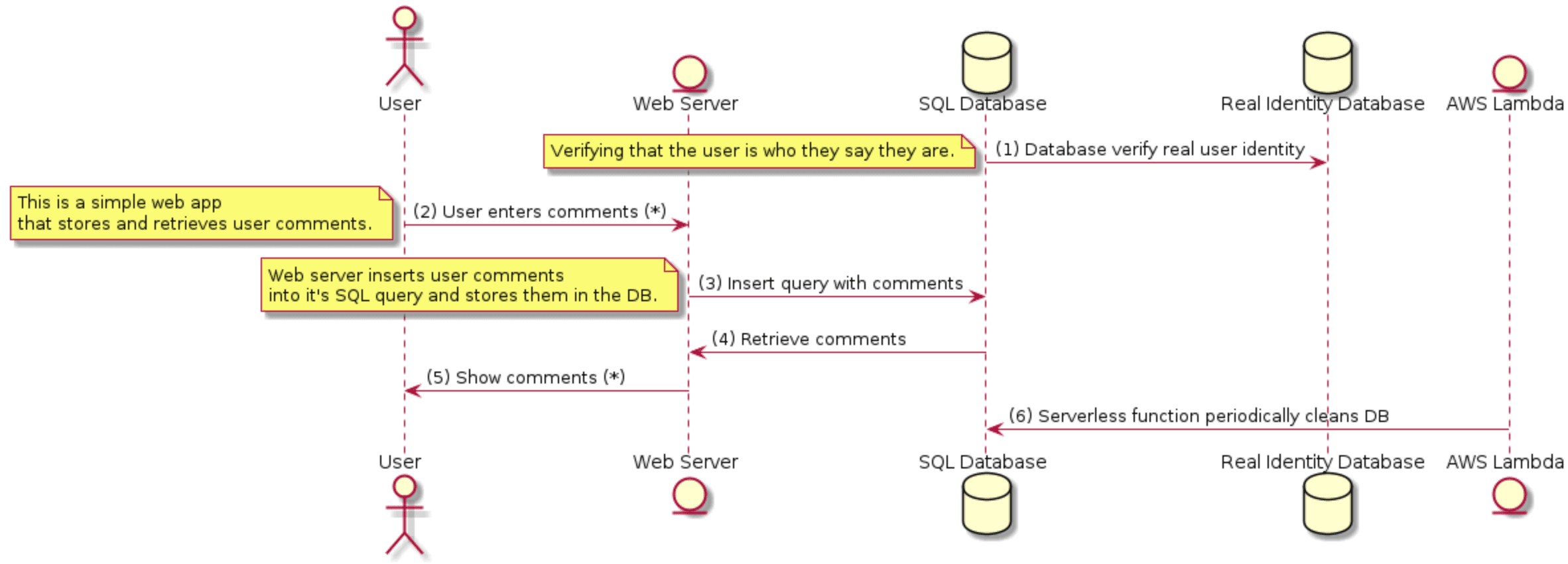
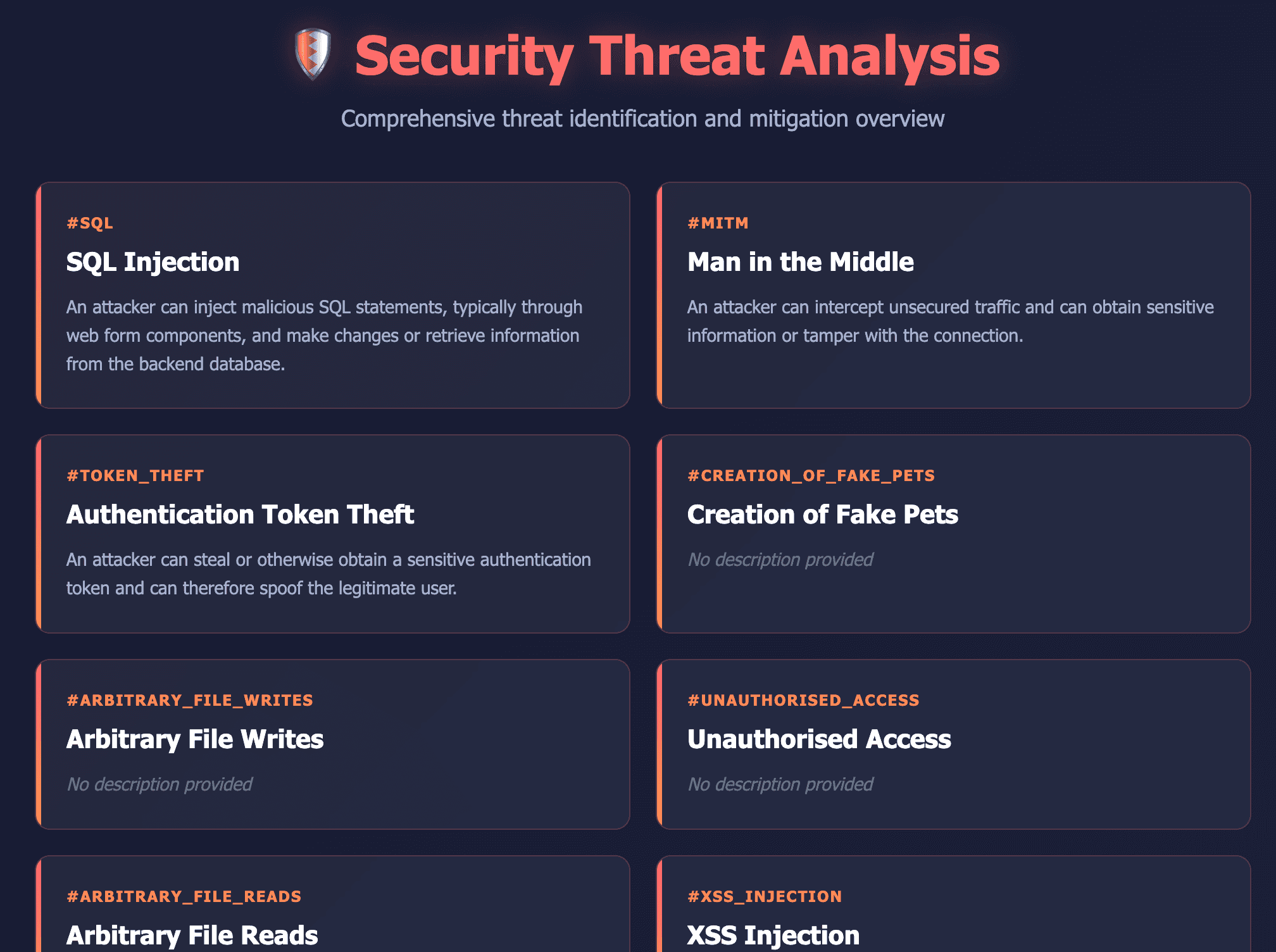
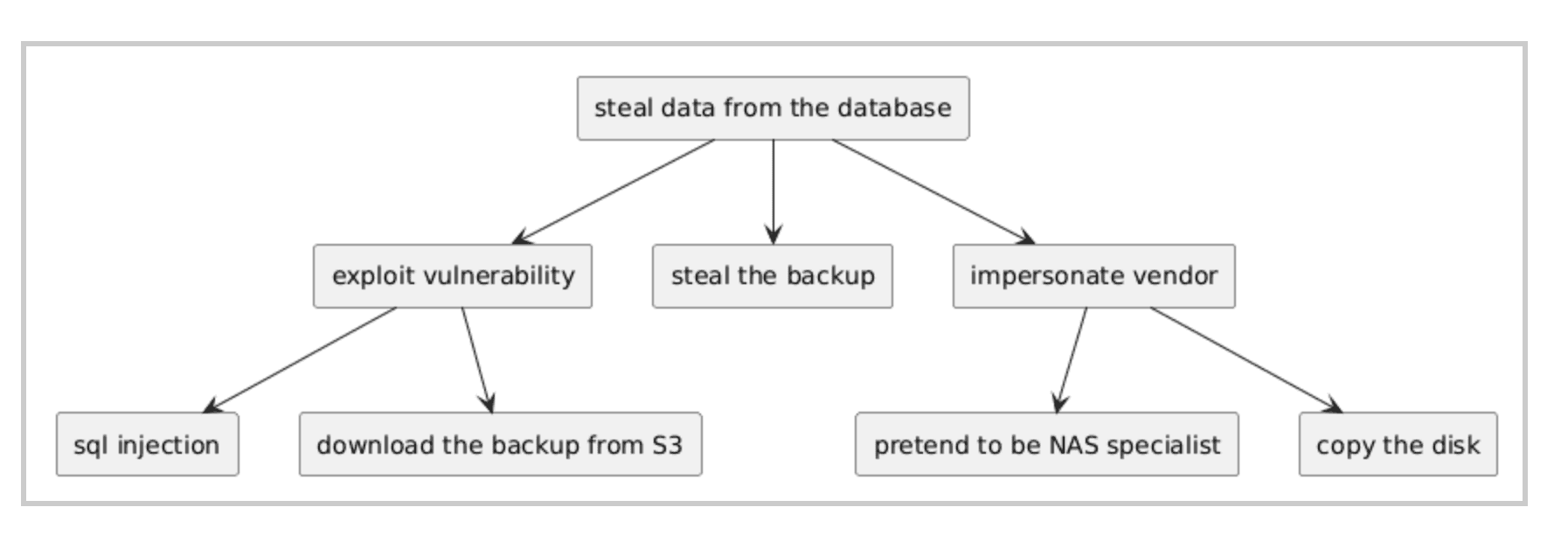
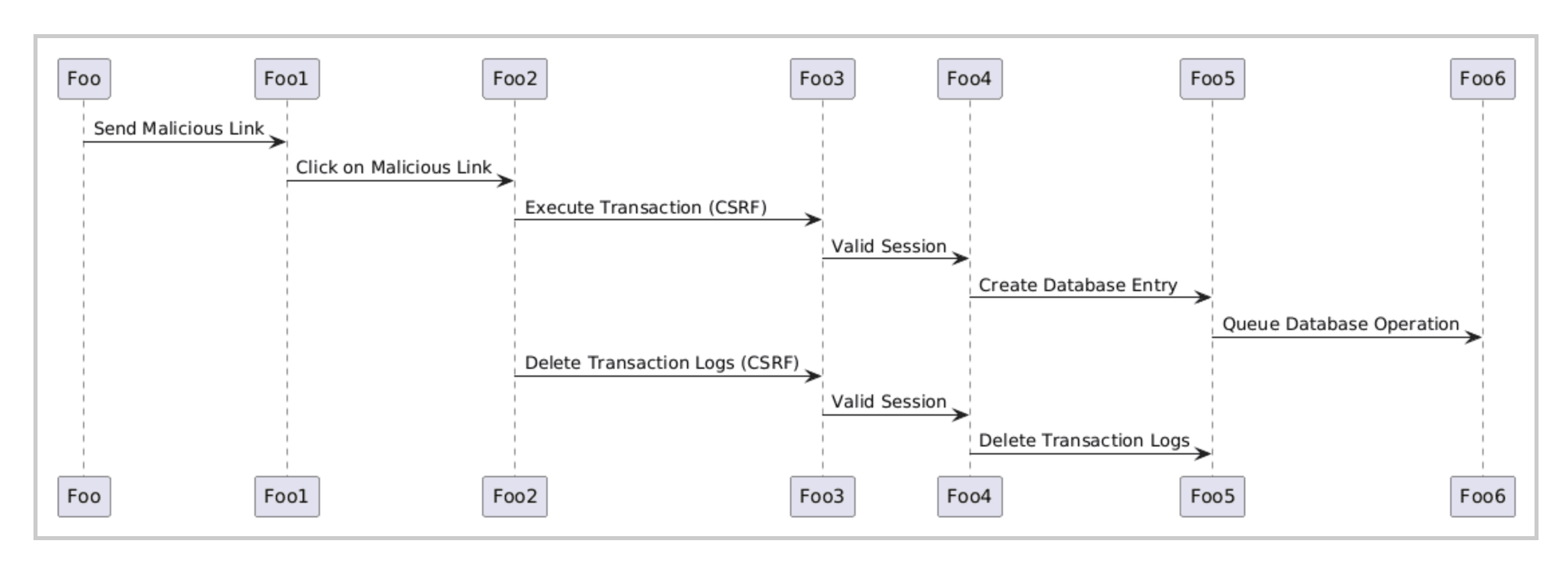
Data Flow Diagram
Traditional Threat Modeling Doesn't Scale
Our approach does. We integrate automation, open-source frameworks, and enterprise workflows to make threat modeling continuous, data-driven, and collaborative.
AI-Powered Automation
Leverage agentic intelligence to automate threat identification, mapping, and mitigation across your entire technology stack.
Framework Expertise
Deep integration with OWASP, MITRE ATT&CK, CAPEC, NIST, ISO 27001/27701, and other industry standards.
Enterprise Integration
Seamlessly connect with your existing tools: Jira, GitHub, GitLab, CI/CD pipelines, and more.
How We Help
Comprehensive services to build and scale your threat modeling practice
Workshops
Learn modern threat modeling through immersive, scenario-based training tailored to your technology stack.
Consulting
Build and operationalize a sustainable threat modeling practice from the ground up.
Coaching
Get expert guidance to mature your internal capabilities and drive continuous improvement.
Integration
Connect open-source and proprietary tools directly into your workflows and CI/CD pipelines.
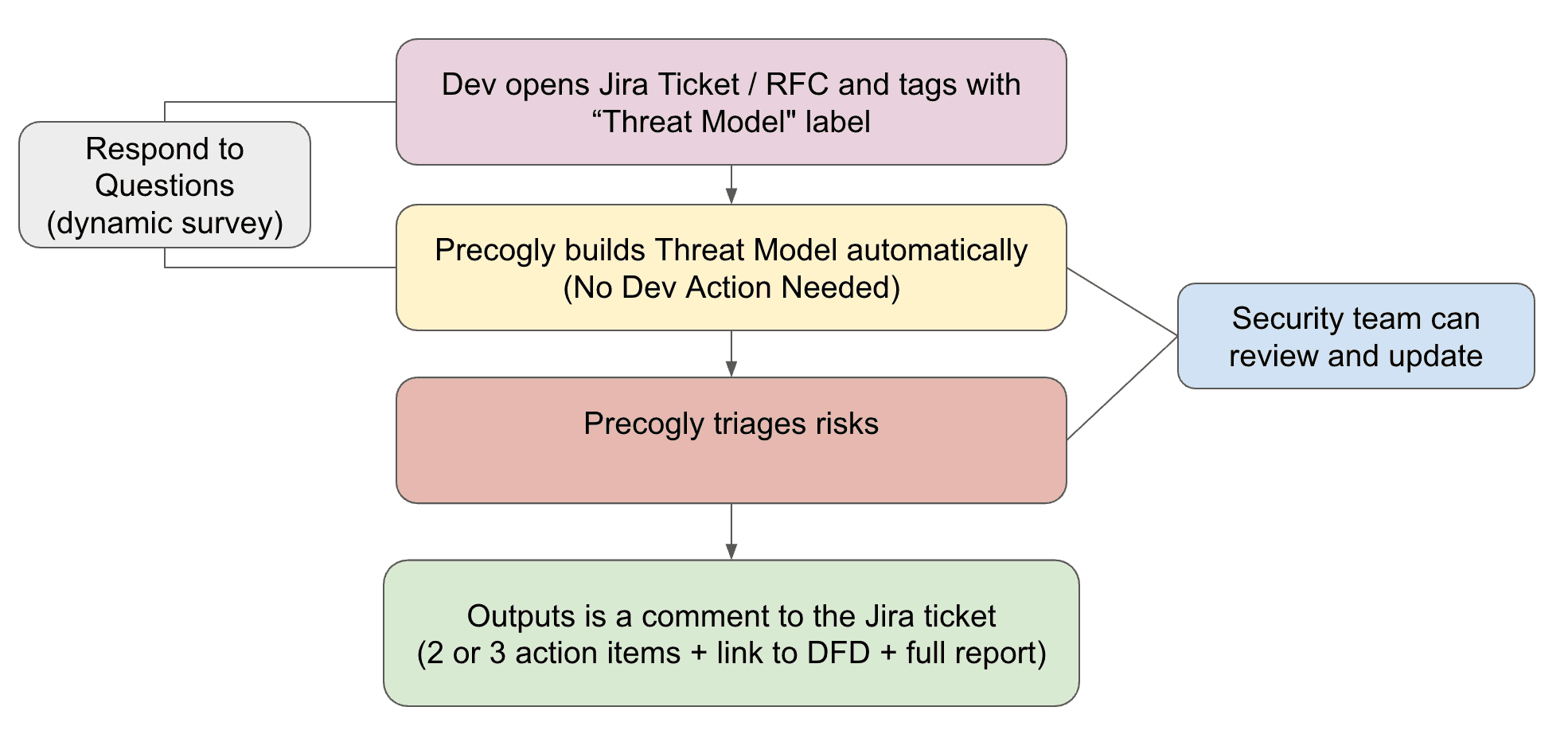
What We Deliver
Our AI Threat Modeling Engine accelerates every stage of the security design process
Survey Intake
Smart questionnaires + artifact mining from PRDs, OpenAPI specs, and Terraform configurations
DFD Generation
Automated Data Flow Diagrams with trust zones, boundaries, and asset identification
STRIDE & LINDDUN
Comprehensive security and privacy threat identification across all system components
Abuse Stories & Attack Trees
Model attacker intent and sequence to understand realistic threat scenarios
CAPEC, ATT&CK & ASVS Mapping
Normalize, detect, and link threats to known attack patterns and verification standards
Compliance Correlation
Map mitigations to PCI DSS, HIPAA, ISO 27001/27701, SOC 2, NIST 800-53, and GDPR
Built on Trusted Foundations
We leverage and integrate with industry-leading open-source frameworks and standards
OWASP
Threat Dragon & PyTM for modeling and automation. Deep integration with OWASP security standards.
MITRE
ATT&CK & CAPEC frameworks for adversary mapping, pattern recognition, and threat intelligence.
OpenCRE
Control traceability across frameworks including NIST, ISO, PCI DSS, and compliance standards.
Also supporting:
Ready to Transform Your Security Practice?
Let's discuss how Ascendus AI can help you build a scalable, automated threat modeling program.
Schedule a ConsultationAbout Ascendus AI
Ascendus AI is a next-generation security consultancy focused on scaling threat modeling through artificial intelligence. The firm brings together expertise in AI, cloud, and secure software design to help enterprises automate and operationalize their threat modeling programs.
Founded by professionals with backgrounds from Carnegie Mellon University and Columbia University, Ascendus AI combines academic rigor with hands-on engineering experience across healthcare, cloud, and enterprise systems. Its team has developed agentic threat modeling tools, AI governance platforms, and machine-learning solutions aligned with OWASP, MITRE, and NIST frameworks.
Get in Touch
Ready to transform your threat modeling practice? We'd love to hear from you.